
In 2024, Klippa researched The State of Automation in Finance and discovered that nearly 50% of the surveyed finance professionals consider duplicate and fraudulent invoices more common than exceptional in their daily operations. Alarmingly, most respondents reported detecting up to 10 fraudulent invoices each month on average.
These findings underscore that accounts payable fraud is a persistent threat to companies of all sizes and across various regions. The significant financial risks associated with AP fraud highlight the need for improved systems within many AP departments, from employee training to the implementation of fraud-prevention software.
But what exactly constitutes AP fraud, and are there vulnerabilities that could make your company more susceptible? Stay with us as we break down the nature of accounts payable fraud, examine some of the most common schemes employed by fraudsters, and offer practical strategies to protect your business.
Key Takeaways
- AP Fraud is Widespread: Nearly 50% of finance professionals encounter fraudulent or duplicate invoices regularly, posing a major financial risk.
- Common AP Fraud Schemes: These include billing schemes, ghost vendors, invoice duplication, kickback schemes, and unauthorized ACH transactions.
- Red Flags to Watch For: Be alert to unusual vendor activity, duplicate payments, altered invoices, rush payment requests, and financial inconsistencies.
- Prevention Strategies: Strengthen security with AP automation, vendor verification, dual-payment authorization, internal controls, and regular audits.
- Technology is Key: Using AI-driven fraud detection, automated reconciliation, and real-time transaction monitoring helps prevent AP fraud effectively.
What is Accounts Payable Fraud?
Accounts Payable Fraud, or AP Fraud, is a type of financial deception that targets any component of a company’s accounts payable systems. Accounts payable fraud schemes range from internal fraud committed by AP employees to external fraud by vendors or an employee and vendor working together.
The most common industries targeted by this type of fraud are traditionally those that regularly deal with several suppliers and large money transfers, such as the real estate, legal, and construction sectors.
One of the most infamous cases of AP fraud involves a scammer who defrauded Alphabet and Meta (formerly Google and Facebook) of $100 million by sending fake emails and invoices over 2 years. This incident serves as a reminder that without proper protection, even some of the biggest technology-based companies can fall victim to invoice fraud.
9 Common Types of Accounts Payable Fraud
In the previous section, we mentioned how even the most technologically advanced companies can be vulnerable to accounts payable fraud. Fraudsters have become highly skilled at utilizing various techniques and complex schemes that are increasingly difficult to detect, especially without the assistance of fraud detection technology.
These fraudulent activities generally fall into two categories: internal and external fraud. Internal or employee fraud is committed by your employees. External fraud, on the other hand, is committed by individuals or entities outside of your company, such as vendors or unrelated parties. Below, we will outline the most common schemes within each category.
Internal AP Fraud
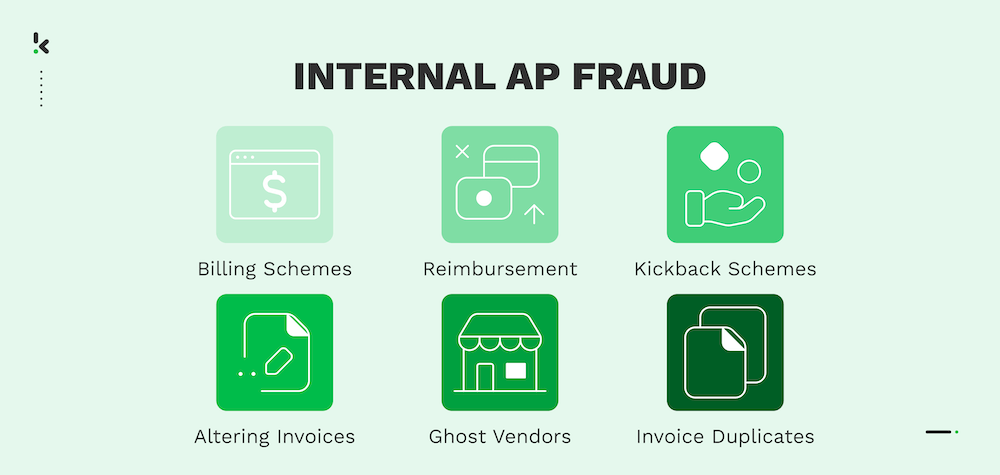

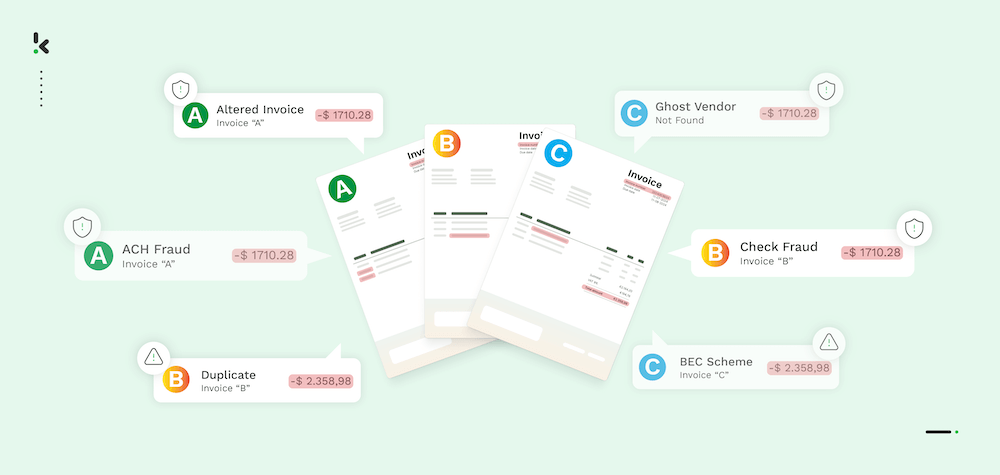
Billing Schemes
In billing schemes, employees may create fictitious invoices from real vendors for goods or services that were never delivered, or they might inflate legitimate invoices to pocket the difference. Some might go as far as establishing a shell company to create entirely fake vendors.
Setting up a shell company involves creating a legitimate-looking but fictitious business, complete with a bank account and tax ID. Such a scheme might be used in large fraud cases, especially where a big vendor deal is involved.
However, for regular employees, simpler methods — like using a personal account under a false name or manipulating existing vendor invoices — are more common.
Expense Reimbursement Fraud
This form of fraud involves workers falsifying expense reports to claim reimbursement for non-business-related expenses or completely fictitious costs. Techniques include submitting receipts for personal purchases disguised as business expenses, inflating the costs of legitimate expenses, or submitting the same receipt multiple times across different reports.
For instance, an employee might purchase a personal item and submit the receipt as a business expense, knowing that many companies don’t closely scrutinize smaller claims.
Kickback Schemes
In kickback schemes, employees collude with external vendors or suppliers to approve inflated or unnecessary invoices in exchange for a share of the profits.
The kickbacks may be disguised as consulting fees, bonuses, or other legitimate payments and are typically funneled through accounts not directly tied to the employee, such as those of family members or associated shell companies.
Altering Invoices
Employees with access to AP systems might change legitimate invoices by altering amounts or payment details to divert funds. For example, they could change the bank account number on an invoice to their own or a controlled account. These changes might be subtle, involving small amounts over time to avoid detection. In many cases, the fraudster might use their bank account or an account under a false name.
Ghost/Phantom Vendors
This type of fraud involves the creation of entirely fictitious vendors within the company’s AP system. The employee sets up these ghost vendors and submits invoices for goods or services that were never provided. Payments are then directed to accounts controlled by the employee, often under the disguise of legitimate business transactions.
Invoice Duplicates
This type of fraud is relatively easy for an insider to commit. Invoice duplication fraud occurs when an employee submits the same invoice multiple times to extract additional payments for the same goods or services. This can happen through outright duplication, where the same invoice is submitted twice, or through subtle variations, such as changing the invoice number or date.
Employees might exploit weak AP software that doesn’t automatically flag duplicate invoices, or they may manually intervene to bypass such checks. To conceal the fraud, the employee might spread out duplicate invoices over time or across different departments.
External AP Fraud
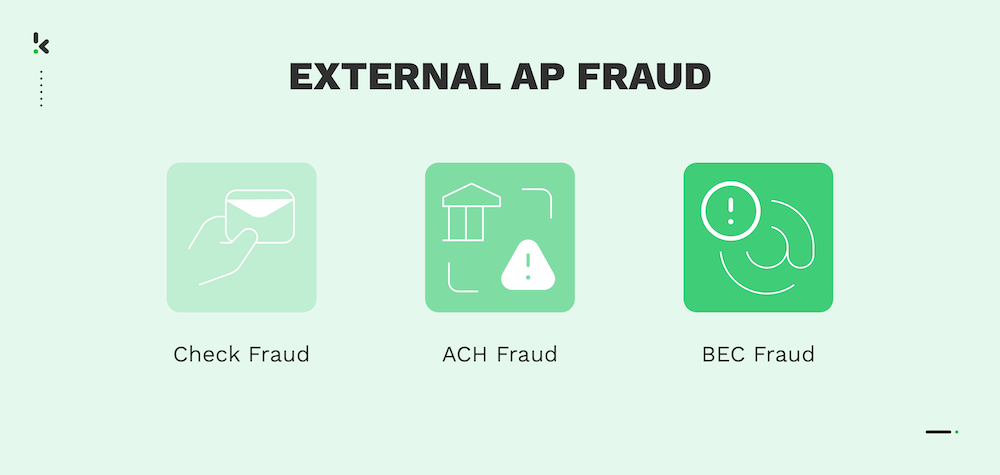

Check Fraud
Check fraud involves the manipulation or theft of physical checks to illegally divert funds. Fraudsters often steal checks from outgoing mail, catching them before they reach their intended recipient. Once obtained, they may alter the check by changing the payee’s name or the amount.
In some cases, fraudsters can use “mules” – individuals recruited to cash checks and forward the money, keeping a small percentage for themselves. Advanced techniques like washing checks (removing ink to rewrite details) are also used, making detection challenging.
ACH Fraud
ACH (Automated Clearing House) fraud typically involves cybercriminals gaining unauthorized access to a company’s bank accounts via phishing, malware, or social engineering tactics. Once they have access, they initiate unauthorized electronic transfers to accounts they control, which could be under fake identities or third-party accounts they have compromised.
To conceal their identity, fraudsters may use a network of mule accounts or even cryptocurrencies, which are harder to trace. ACH fraud is particularly insidious because it can occur without any physical interaction, making it difficult to detect until significant damage has already been done.
Business Email Compromise (BEC)
In BEC schemes, fraudsters impersonate a trusted figure, such as a vendor or senior executive, through compromised email accounts. They then send urgent requests to the AP department, instructing them to make payments to fraudulent accounts.
These accounts are usually set up using fake identities and are closed shortly after receiving the funds to avoid detection. The emails are crafted to look authentic, with similar language, signatures, and even timing that aligns with the victim’s business practices, making them difficult to spot.
Why Companies Fall Victim to AP Fraud
Identifying why your company might be susceptible to accounts payable fraud is critical for prevention. Here’s a closer look at the key risk factors that can make your organization vulnerable:
- Over Reliance on Manual Processes: Manual processes, like entering invoice data by hand or using paper checks, introduce opportunities for fraud. For instance, an AP employee might manipulate invoice amounts or create fake invoices from legitimate vendors, knowing that manual processes lack effective audit trails. Manual checks can also be duplicated or altered after being issued.
- Lack of Segregation of Duties: In many small to mid-sized companies, it’s common for a single person to receive invoices, book them, process payments, and reconcile the bank statements. If an AP clerk is responsible for both processing vendor invoices and issuing payments, they could easily approve a fraudulent invoice or divert payments to a personal account without immediate detection.
- Inadequate Vendor Management: Companies often fail to maintain an up-to-date, vetted list of vendors. For example, a lack of thorough vendor verification might allow a fictitious company to be added to your system. Payments could then be made for goods or services that were never delivered, often without anyone noticing until it’s too late.
- Weak Internal Controls: If your company allows manual overrides in your AP system without requiring a secondary approval, an employee could exploit this to alter payment amounts or redirect funds. Additionally, if invoice approval workflows are not enforced, invoices might be paid without proper authorization, increasing fraud risk.
- Inconsistent Reconciliation Practices: Invoice reconciliation is often seen as a routine task and can be neglected or rushed, especially during busy periods like month-end closing. For example, if your AP team regularly delays reconciling AP records with bank statements, discrepancies such as duplicate payments or unauthorized withdrawals may go unnoticed.
- Irregular Audits: Skipping regular internal audits or only conducting superficial checks can leave fraud undetected for extended periods. For example, if your company doesn’t regularly audit the entire AP process, a long-running scheme, such as a ghost vendor set up by an insider, might continue unnoticed, leading to significant financial losses.
These practical examples illustrate how common vulnerabilities can lead to significant risks in your accounts payable process. Understanding these factors helps you recognize potential weaknesses in your own system so you can take steps to mitigate them.
How to Spot Accounts Payable Fraud: 9 Red Flags
Detecting accounts payable fraud early can save your company significant financial loss. By staying alert to some red flags, you can detect AP fraud and take swift action to mitigate the damage. Awareness and vigilance are your first lines of defense in protecting your company’s finances.
Here are some red flags that you should be on the lookout for:
- Unusual Vendor Activity: Be wary of vendors that suddenly start invoicing more frequently or in higher amounts than usual. Also, keep an eye out for vendors with similar names to existing ones, which might be an attempt to create a fake vendor profile.
- Duplicate Payments: Repeated payments for the same invoice or the same amount can be a sign of fraud. For instance, if you notice two payments made to the same vendor for identical amounts on the same date, it could indicate that someone is intentionally duplicating payments and diverting funds to a personal account.
- Invoices Without Purchase Orders: Receiving invoices that don’t match any existing purchase orders (POs) is a common red flag. An invoice might be submitted for goods or services never ordered or received. Always question invoices that don’t have a corresponding PO or contract.
- Vendor Information Changes: Sudden changes in vendor details, such as bank account information or contact addresses, should raise suspicion. For instance, if a vendor requests that payments be sent to a new bank account, especially on short notice, it’s essential to verify this change independently before processing any payments.
- Rush Payment Requests: Be cautious of requests for urgent payments that bypass normal review processes. For example, if an employee insists that a vendor must be paid immediately and asks to skip the usual approval steps, it could be an attempt to push through a fraudulent payment. Rush requests are often used to exploit time-sensitive situations.
- Round-Number Invoices: Invoices that are consistently rounded to whole numbers (e.g., $5,000 or $10,000) can be suspicious, especially if they don’t reflect the typical pricing or billing practices of the vendor. Fraudsters often use round numbers to make their fraudulent invoices blend in, but this can also make them stand out under scrutiny.
- Unexplained Variances in Financial Reports: Significant or unexplained discrepancies between budgeted and actual expenses can indicate fraud. For example, if a particular expense category regularly exceeds the budget without a clear reason, it could mean that fraudulent invoices are being processed.
- Altered or Forged Documents: Documents that appear to be tampered with — such as invoices with corrections, inconsistent fonts, or missing information — are a clear red flag. For instance, if an invoice number seems altered or the vendor’s contact information is incomplete, it could be a sign that the document is fraudulent.
- Unusual Patterns in Check Numbers or Payment Dates: Sequential check numbers or payments made on unusual dates (such as weekends or holidays) should be investigated. For example, if several checks are issued in sequence to the same vendor, it could indicate that someone is trying to hide fraudulent activity by issuing payments when scrutiny is low.
How to Detect AP Fraud using Benford’s Law?
Benford’s Law is a useful tool for spotting anomalies in financial data, such as AP transactions. It predicts that in naturally occurring datasets, smaller digits, like 1 and 2, appear as the leading digit more frequently. For instance, the digit 1 should be the first digit in about 30% of cases.
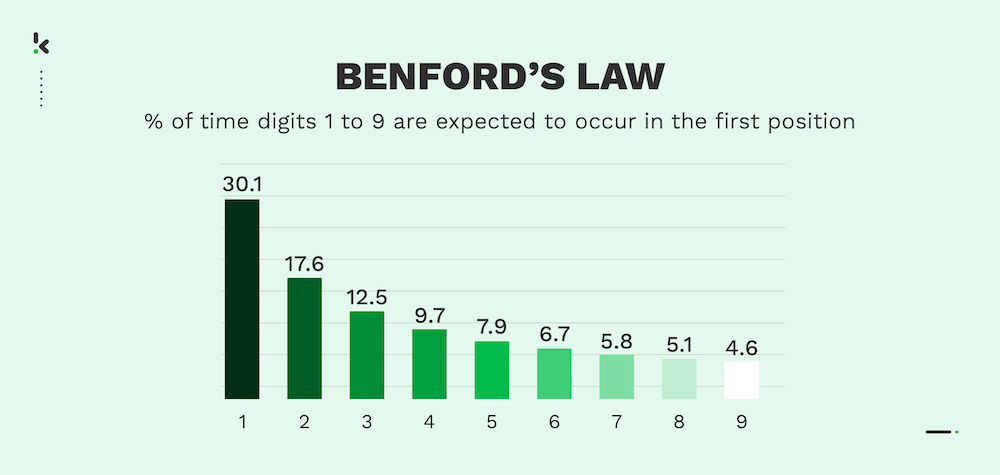

If you apply Benford’s Law to your payment data and notice that certain digits, like 7 or 8, appear more often than expected as the first digit, it could indicate manipulated or fraudulent numbers. While it’s not definitive proof, these deviations are red flags that warrant further investigation into the suspicious transactions.
How to Investigate Accounts Payable Fraud
When red flags suggest that accounts payable fraud may be occurring, a thorough and methodical investigation is essential to take appropriate action. Here’s how you can effectively investigate suspected AP fraud:
1. Initiate an Internal Investigation
The first step in responding to suspected fraud is to launch an internal investigation. This involves gathering all relevant documentation, such as invoices, purchase orders, payment records, and correspondence. Start by isolating transactions or vendors that triggered the red flags.
For example, if duplicate payments were flagged, pull all records related to those transactions and review them for irregularities, such as altered invoices or inconsistent payment details.
2. Conduct a Detailed Audit
Once you’ve gathered initial evidence, a detailed audit should follow. This audit might involve reviewing months or even years of AP transactions to identify patterns that could indicate fraudulent activity. Look for unusual payment patterns, such as round-number payments, multiple payments to the same vendor in a short period, or payments to vendors with similar names.
In addition, cross-check vendor records with external databases to ensure their legitimacy and verify that the goods or services billed were actually received. This audit should be conducted independently, ideally by someone outside the AP department.
3. Leverage Third-Party Auditors
If the fraud appears complex or extensive, bringing in third-party auditors or forensic accountants can provide a fresh perspective and specialized expertise. These professionals can conduct a deeper analysis of financial records, using advanced techniques such as data analytics to spot inconsistencies that might not be immediately obvious.
4. Interview Key Personnel
Interviewing employees involved in the AP process is a critical component of the investigation. Start with those directly handling the flagged transactions, but also include others in related roles.
During interviews, ask about unusual activities, such as rushed payment requests or changes in vendor payment details. It’s important to create an environment where employees feel safe to share information, as they may provide crucial insights into the suspected fraud.
5. Review Whistleblower Reports
Whistleblowers often provide valuable information that can uncover fraud. If your company has a whistleblower policy, review any reports related to the AP department. Ensure that these reports are handled with care, protecting the identity of the whistleblower to encourage others to come forward with information.
For example, if a whistleblower reports suspicious behavior by an employee managing vendor payments, closely examine that employee’s transaction history and look for any connections to fraudulent activities.
Steps to Take After Discovering AP Fraud
Once the investigation is complete, compile your findings into a report. This report should detail the nature of the fraud, how it was carried out, who was involved, and the financial impact on the company. Based on these findings, take appropriate action, whether that means correcting internal processes, pursuing legal action, or improving controls to prevent future fraud.
Throughout the investigation, it’s essential to involve your legal and HR departments. Legal counsel can provide guidance on how to handle evidence and ensure that the investigation complies with relevant laws and regulations. HR can assist in managing employee relations, especially if disciplinary action is required.
9 Ways to Prevent AP Fraud in Your Company
Preventing accounts payable fraud requires an approach that combines best practices, strong internal controls, and the right tools. Here’s how you can protect your company against AP fraud:
1. Use Accounts Payable Software
If you want a solution to AP fraud that could bring immediate benefits and results to your AP team, investing in reliable accounts payable software is the best choice. Modern AP software automates invoice processing, approval workflows, and payment execution, making it harder for fraudulent invoices to slip through with the help of AP automation.
For instance, AP software can flag duplicate invoices, prevent unauthorized changes to vendor details, and maintain an audit trail of all transactions. Additionally, it can integrate with your enterprise resource planning (ERP) system, providing real-time visibility into your activities for accurate and complete accounts payable management.
2. Implement Strong Internal Controls
Establishing robust internal controls is the first line of defense against AP fraud. This includes separating duties within the AP process. For example, the person who approves invoices should not be the same person who processes payments. Segregation of duties ensures that no single employee has too much control over the payment process, reducing the risk of fraud.
3. Conduct Regular Audits
Regular internal and external audits are crucial for detecting and preventing fraud. Schedule audits periodically to review AP transactions, vendor payments, and reconciliation processes. For example, an internal audit might uncover irregularities such as payments to inactive vendors or discrepancies between purchase orders and invoices.
4. Vet and Monitor Vendors
Ensure that all vendors are thoroughly vetted before being added to your system. This includes verifying their legitimacy, checking their financial health, and understanding their business practices. Regularly update and review your vendor list to remove inactive or suspicious vendors.
For instance, AP software can automatically monitor vendor activity and flag unusual patterns, such as vendors invoicing at a higher frequency or using a different IBAN in their payment requests.
5. Enforce Dual Authorization for Payments
Require dual authorization for all significant payments. This means that two individuals must approve any transaction above a certain threshold. For example, AP software allows users to apply multi-level authorization flows based on applied business rules (e.g., if a payment exceeds $10,000, it should require approval from both an AP manager and a senior executive).
This additional layer of oversight makes it harder for fraudulent payments to be processed without detection.
6. Train Employees on Fraud Awareness
Educate your AP team about accounts payable fraud risks and how to recognize it. Regular training sessions should cover common fraud schemes, red flags to watch for, and the importance of following established protocols.
7. Utilize Data Analytics and Benford’s Law
Leverage data analytics to monitor AP transactions for anomalies that could indicate fraud. Tools that apply Benford’s Law can help detect irregularities in payment amounts by analyzing the distribution of leading digits. For instance, if you notice that certain numbers appear more frequently than expected as the first digit in payment amounts, it could signal manipulation or fabricated invoices.
8. Encourage Whistleblowing
Create a safe and confidential way for employees to report suspected fraud. A whistleblower policy encourages employees to come forward without fear of retaliation. For example, a secure, anonymous reporting system can help uncover fraudulent activities that might go unnoticed.
9. Regularly Reconcile Accounts
Timely and regular reconciliation of your AP records with bank statements and general ledger entries is essential. This helps you catch discrepancies early, such as payments that don’t match recorded invoices or unauthorized withdrawals. Set up a routine schedule for reconciling accounts weekly or monthly to ensure that all transactions are accounted for and legitimate.
Shielding your company from accounts payable fraud means a combination of all the above-listed techniques, and no other tool combines as many best practices and fraud-prevention mechanisms as accounts payable software.
Eliminate Accounts Payable Fraud with Klippa
Stop AP fraud in your company by automating vendor invoice processing with an accounts payable solution. Gain control over your APs by eliminating paper-based workflow, manual data entry, and unsupervised physical approvals with Klippa SpendControl.
Klippa SpendControl is an all-in-one digital pre-accounting software that combines invoice processing, expense management, and corporate credit card modules for all your AP needs.
Our software utilizes Optical Character Recognition (OCR) technology to ensure 99% accurate invoice data capture, which eliminates manual data entry for secure approval, archiving, and booking of checks directly to your financial administration.
- Manage your invoices, expenses, and credit card transactions in one platform
- Submit, process, and approve invoices via web or mobile app
- Prevent invoice and expense fraud with built-in duplicate and fraud detection
- Customize your approval management with multi-level authorization flows
- Automatically detect vendors with incorrect or potentially fraudulent IBANs
- Get real-time insights into your accounts payable with our intuitive dashboards
- Rely on automatic multi-currency support for international payments
- Never fail to comply with tax and data privacy regulations with our ISO27001-certified and GDPR-compliant solution
- Integrate SpendControl with your accounting and ERP software, like Quickbooks, NetSuite, or SAP
FAQ
An example of accounts payable fraud is submitting duplicate invoices to extract multiple payments for the same goods or services.
AP fraud can be detected by implementing strong internal controls, conducting regular audits, using AP automation software, and monitoring for red flags like duplicate payments or unusual vendor activity.
The risks of AP fraud include significant financial loss, damaged vendor relationships, and potential legal consequences.
Avoid fraud in accounts payable by using AP software, enforcing segregation of duties, conducting regular audits, vetting vendors thoroughly, and requiring dual authorization for large payments.
Red flags of AP fraud include unusual vendor activity, duplicate payments, invoices without corresponding purchase orders, sudden changes in vendor information, and rushed payment requests.