

In an era when technology advances at the speed of light, cybercrime has become even more apparent. One of its most common types is identity theft. In fact, according to a Javelin Strategy & Research study, more than 40 million US consumers had their identity stolen in 2021.
At the same time, more data is being stored online (e.g. a client’s personal information). This requires stricter monitoring and protection of your security systems, avoiding fraudsters to gain access to private data and making sure people are who they claim to be.
For many years, fingerprint scanning provided the world with proper security, being the preferred biometric verification type in most cases. However, technologies have developed since then, giving us faster, easier to use and more accessible ways of verifying people’s identities. A good example of such a technology is facial recognition.
Since being introduced for the first time, face recognition technology has become massively popular, especially amongst smartphone users. Apple implemented this method (Face ID) in all its products, stating on its launch, in 2017, that it was up to 20 times more secure than its previous biometric verification method: fingerprint scanning, also known as Touch ID.
If your business is subject to anti-money laundering (AML), General Data Privacy Regulations (GDPR), and Know Your Customer (KYC) procedures, you have probably asked yourself which biometric verification type – fingerprint scanning or facial recognition – is the best option to implement.
In this blog, we’ll discuss the differences between these two biometric authentication methods, their pros and cons, and why facial recognition might be the best choice for your KYC process.
Differences between Fingerprint Scanning and Facial Recognition
There’s no denying that the use of biometrics for verification has been very favorable to companies in verifying people’s identities. However, many still wonder what distinguishes fingerprint scanning from facial recognition. Let’s take a look at their main differences, pros and cons.
What is Fingerprint Scanning?


Fingerprint scanning is a way to verify your identity by scanning and capturing an image of your fingerprint and converting it into a digital template.
This biometric verification method needs a sensor (fingerprint reader) in order to obtain a high-quality image of the fingerprint. It requires a combination of software and hardware to match and identify an individual through fingerprints.
Pros of Fingerprint Scanning:
- Fast: Ultimately, fingerprint recognition helps speed up the process of logging into a system or accessing a service, thus eliminating the need for users to remember passwords.
- Easy to use: Using a finger scanner is straightforward and simple. Just put your finger on the reader and it will do the rest.
- Less intrusive: Some people feel safer using fingerprint scanning as they consider it to be less of a privacy infringement.
Cons of Fingerprint Scanning:
- Expensive hardware required: To use this technology, you will need a fingerprint scanner, something not every device has. In the mobile market, they are often found on high-end phones. They are more scarce on laptops and computers, especially when compared to cameras for facial verification.
- Physical contact is needed: In order for the fingerprint scanner to work, real physical contact is required. This may be inconvenient at some times, like when your fingers are dirty or you are carrying something with both hands.
- Low accuracy: The accuracy of this biometric method is limited if your finger is dirty, wet, or you are wearing gloves. It could also be that you are not approaching it at the right angle for it to funcion. Always annoying, right?
What is Facial Recognition?
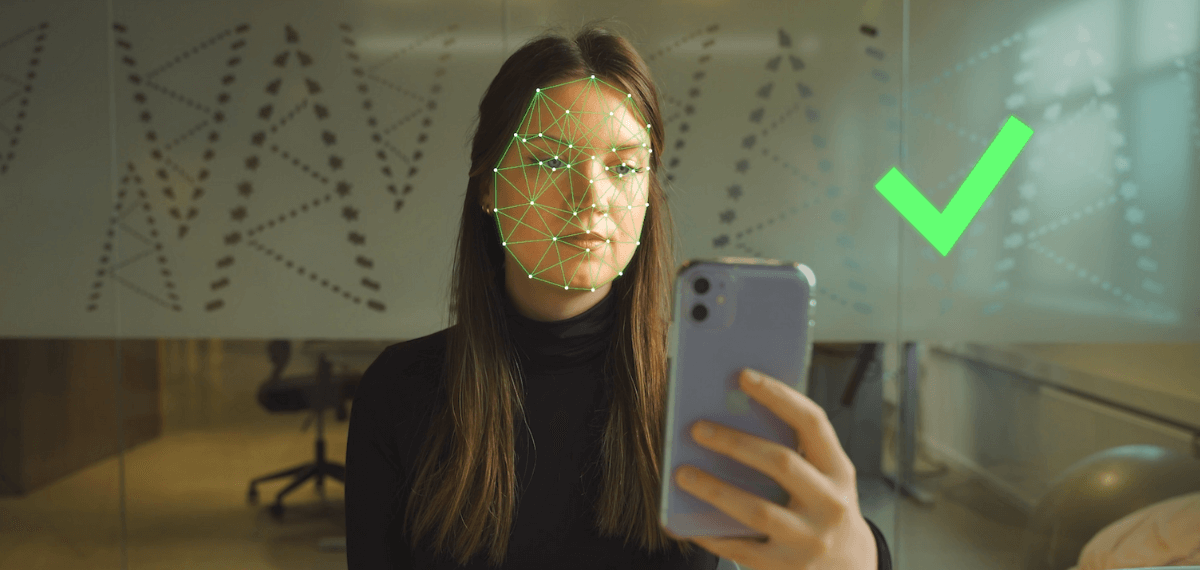

Facial recognition is the method of identifying and recognizing someone through facial biometrics. It captures people’s facial features, digitizes its data points and matches them to a database or an ID document.
With modern technologies such as AI and Machine Learning, facial recognition can be done from a digital image (selfie verification) or a video.
Facial recognition can be used for various operations, such as detecting similarities between two faces (facial matching), identifying one person from a large group of people and finding out whether someone is who they say they are (identity proofing).
Pros of Facial Recognition:
- Simple and convenient: Unlike biometric fingerprint recognition, facial verification doesn’t require a specific scanner or hardware nor contact with the device to work. It can be done with any device containing a camera and is as easy as taking a selfie.
- Secure and accurate: Replicating facial information is very demanding, making this method of biometric verification precise and ideal for protecting sensitive data.
- Fast: When compared to other biometric identification techniques like fingerprint scanning, facial recognition is a quicker technology that offers a seamless and automatic verification process.
Cons of Facial Recognition:
- Privacy concerns: Some people fear having their photos collected and stored in an unknown database. For that reason, not every user likes sharing their personal photos for verification, which is essential for this technology to function.
- Regulatory issues: In some countries, there could be a few challenges when it comes to adopting laws and regulations for the use of this technology.
- Needs controlled environment: The environment is crucial for the success of a facial recognition system. Obstructions like glare from glasses or illumination may cause decline in accuracy. For that reason, real-time feedback is required to improve the precision and user-friendliness of this verification method.
Facial recognition as the standard for ID verification
The demand for digital onboarding has increased as companies try to digitize manual operations while speeding up online registration processes. Regulations like KYC, GDPR and AML have been implemented to protect client identification through security checks and to prevent potential usage for illegal activities such as money laundering, identity theft and identity spoofings.
When it comes to onboarding and KYC processes, facial recognition has been a helpful tool for banks, insurance firms, healthcare, and many more, by simplifying initial registration and adding an additional degree of protection to their systems.
That comes as no surprise, because, as we’ve seen, facial recognition is a secure, fast, accurate and convenient verification method. Unlike fingerprint scanning, it doesn’t require any additional scanner and can be simply done with a camera, which most devices currently have.
These are the reasons why facial recognition technologies are widely used nowadays. The entire procedure may be completed with just one picture of the user. It is also simple to include into digital operations, in which users’ identities must be confirmed, as it can be used on any device with a camera.
While facial recognition is the new standard method for ID verification, there are other methods that may be relevant for your organization.
Other methods of ID Verification
There are many techniques of identity verification, operating in various ways. Some may require biometrics, others might need a chip of an ID document.
Below, we have listed other popular ID verification methods:
- Liveness Detection
- NFC-based Identity Verification
- MRZ Scanning
Liveness Detection


People’s identities can be verified much more securely with the use of liveness checks.
It works by taking a video or a series of selfies in real time to determine whether the source is a real person or an imitation, therefore being a very precise method against spoof attempts.
There are two different types of liveness detection: passive and active.
- Passive liveness analyzes and detects liveness using a single image, which only takes a few seconds.
- Active liveness, on the other hand, can take longer as it requires an action from the user. For instance, users can be given instructions to move their heads in various ways. This makes it impossible to fraud the verification method by using fake images.
Nowadays identity verification is already very hard to bypass with fraud, but high risk industries might still prefer the use of liveness detection.
NFC-based Identity Verification


NFC-based identity verification is a fast, secure and reliable way to streamline your onboarding processes, using technology to read encrypted data in the RFID chip of identity documents. Identity documents with RFID chips are nearly impossible for fraudsters to forge.
By simply using your smartphone or an external NFC card scanner, NFC technology allows you to retrieve data from an identity document, like an ID card or passport, verifying its legitimacy. Next to that, retrieving data from these documents with NFC is often 100% accurate.
MRZ Scanning
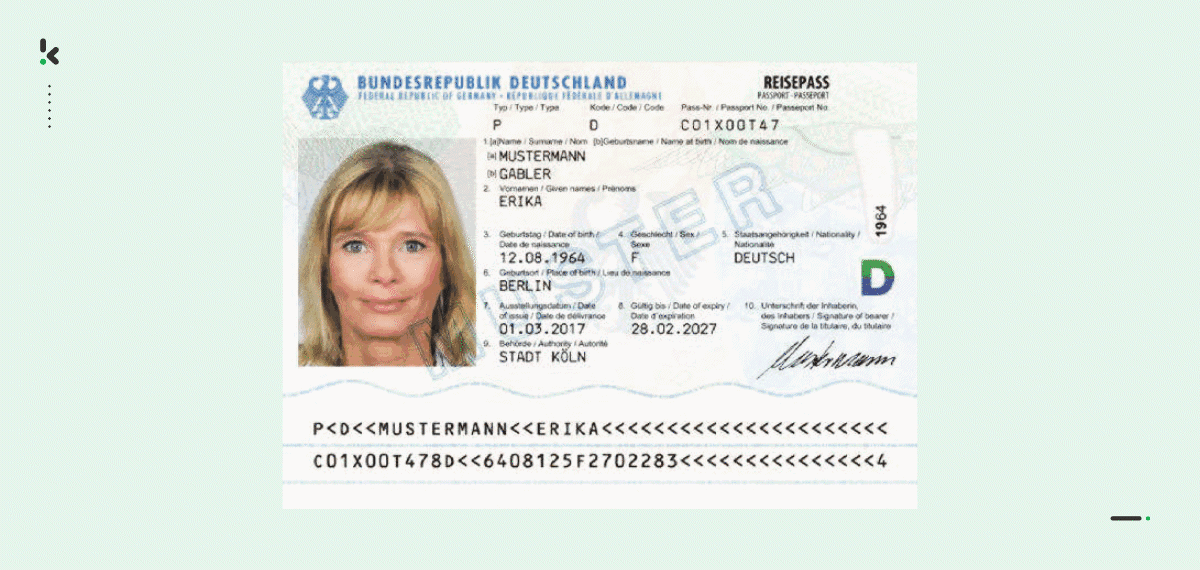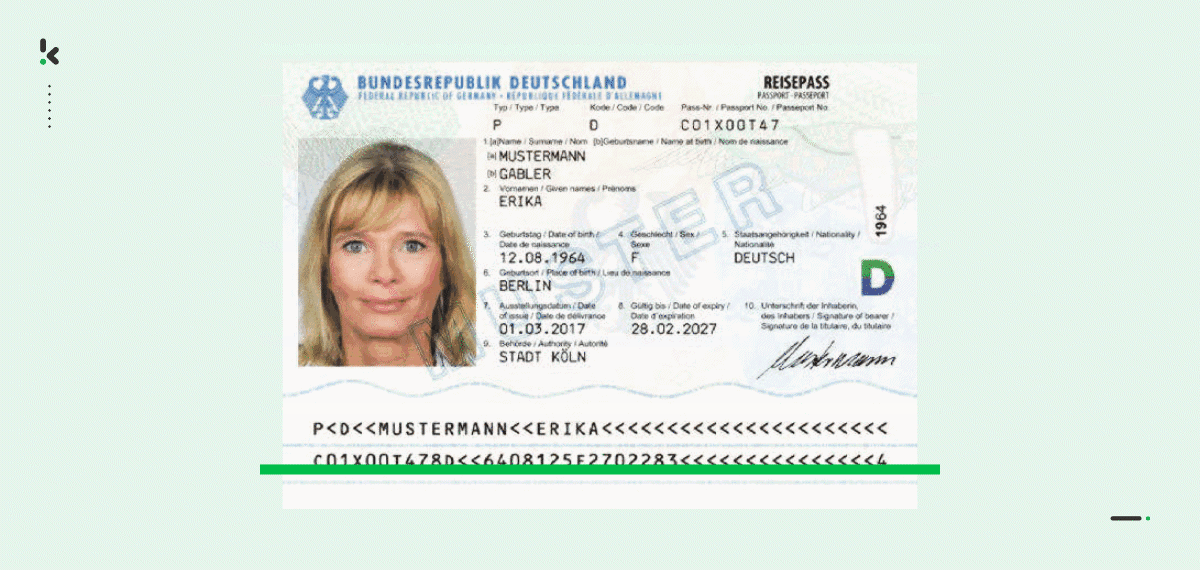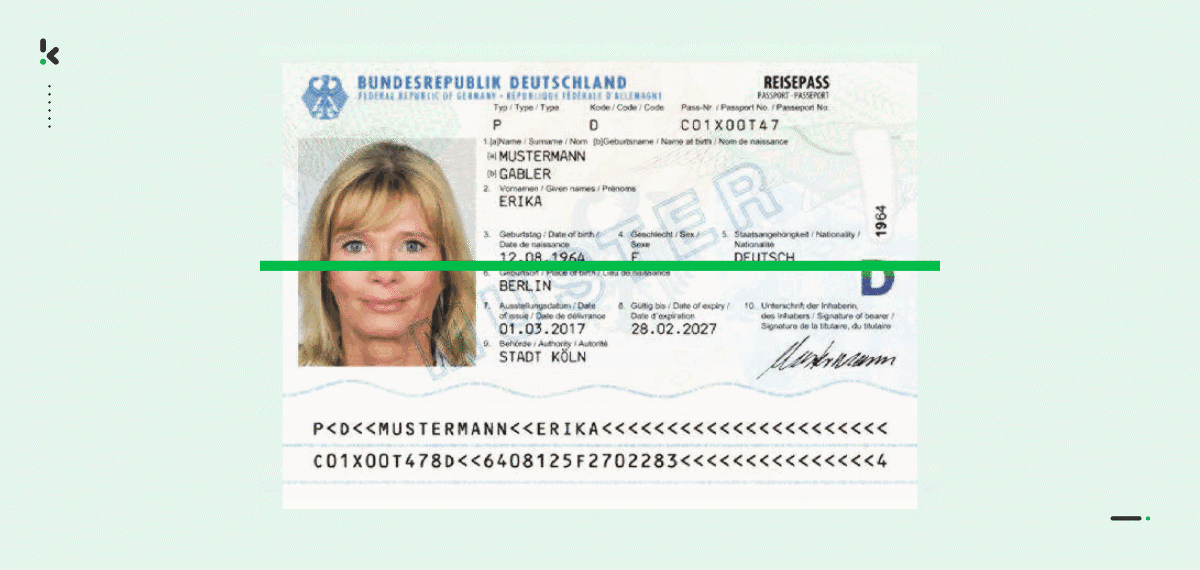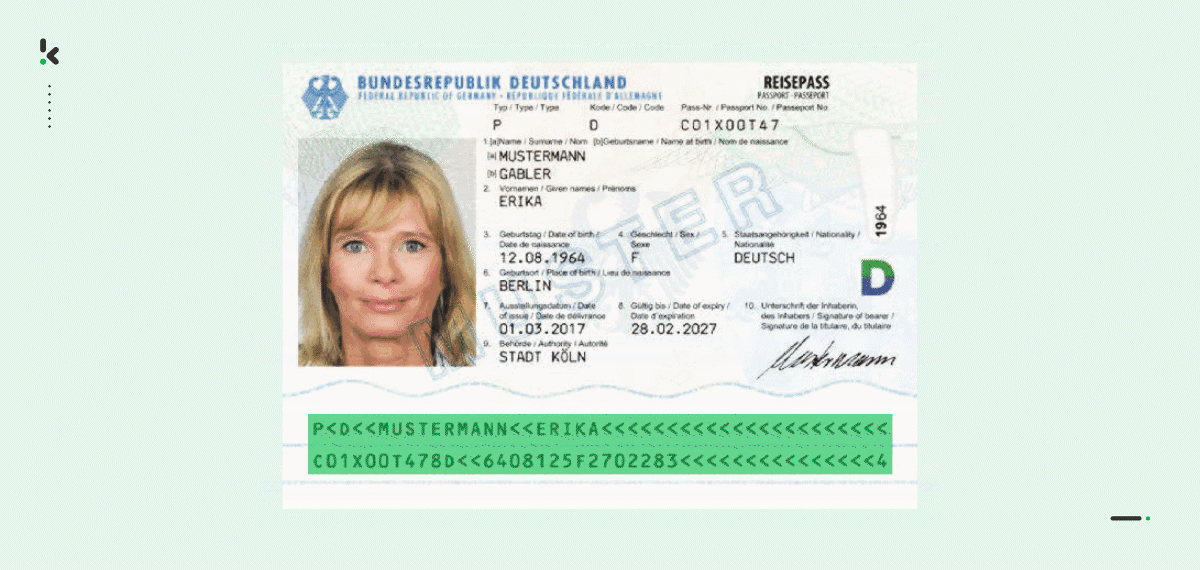

With the help of Optical Character Recognition (OCR) software, like Klippa DocHorizon, you can easily digitize data of a Machine Readable Zone (MRZ).
When reading an MRZ, you can accurately and quickly extract various data fields, such as the name, nationality, date of birth, document number, and many more, thus allowing you to simplify your onboarding and KYC processes.
Why Klippa is the best option for ID verification
Are you still debating on which biometric verification method to implement in your business? Well, you don’t have to debate any longer, as Klippa can help you secure your identity verification processes.
Klippa’s robust automated ID verification solution helps businesses streamline their customer onboarding process while enhancing regulatory compliance. It uses facial recognition, NFC, data extraction, age verification, document fraud detection, selfie scans, and liveness detection with the help of AI and Machine Learning. With the software, you no longer need to worry about spoofing, document fraud, minors accessing restricted services, or identity theft.
Our AI identity verification can be customized to fit into your identity verification flows via SDK or API. And the best part is that Klippa’s solutions are GDPR compliant. This means that no data is stored on Klippa’s servers, so you never have to worry about possible data breaches.
Curious to know more about Klippa’s identity verification solution? Simply schedule a free demo below or contact our team of experts.