
In the first three months of the year, the US National Council on Identity Theft Protection has already registered 5.7 million identity theft reports. This alarming number emphasizes how easy it can be nowadays to be a target of identity theft and how important it is to protect sensitive data, especially when it comes to personal information.
Identity theft comes with great risk that can leave individuals and companies with financial losses and compromised information. As personal data is lost in a data breach, hackers use this information to pursue fraudulent activities or impersonate other individuals, for their own troublesome benefit.
These types of fraud occur due to a poor cyber-security system and a weak identity-proofing process. A simple “username and password” security measure is not enough to protect sensitive data or verify one’s identity anymore. Technology has evolved, but so did hackers’ abilities to gain access to personal information.
In order to add an additional layer of security to their database, more and more companies have chosen to implement an identity-proofing system. If you aren’t familiar with the term yet, keep reading to get acquainted with what identity proofing is and what it entails.
In this blog, we will find out what identity proofing is, its importance, the types of identity proofing and authentication, and lastly, we will offer you an overview of how biometric identity proofing can benefit your business.
What is Identity Proofing?
Identity proofing is the process of verifying a user’s identity to confirm they are who they claim to be. This process takes place by matching the information the user provided during onboarding with the information they give when trying to access their account.
Identity proofing adds another layer of verification to the existing verification process. The traditional way identity proofing is done is by manually comparing the personal information of a user to the data they have provided during onboarding. This manual task is carried out by one of the company’s employees, and it mostly refers to checking information such as phone number, address, and social security number.
However, there is an alternative to the traditional kind of identity proofing, and that is biometric verification. This type of identity-proofing solution uses more complex measures, such as fingerprints, facial recognition, and even iris recognition. This is especially secure as these unique features are impossible to forge or duplicate, therefore sensitive data cannot be accessed by unauthorized users.
Now that we know more about identity proofing, let’s delve deeper and find out how it actually works.
How Does Identity Proofing and Authentication Work?
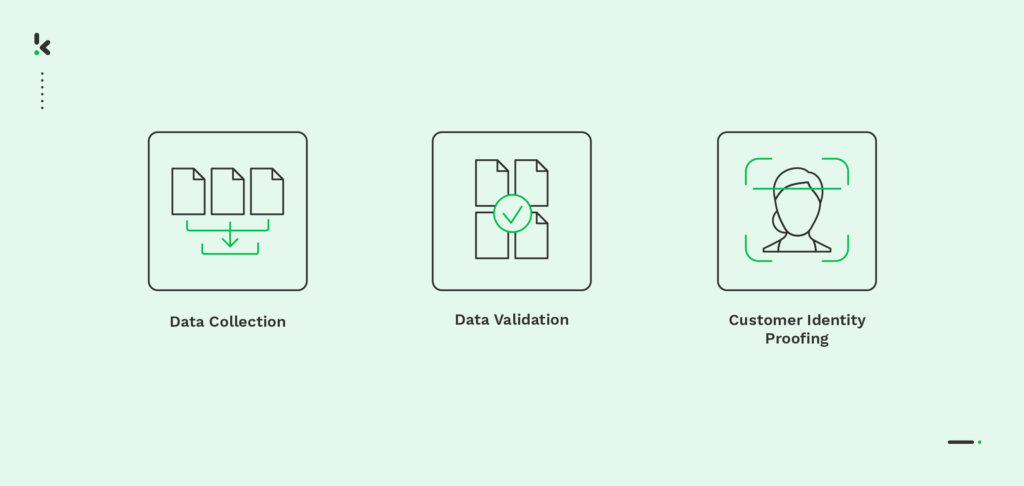

The process behind identity proofing consists of three steps, which we will now discuss in detail:
- Data Collection: The organization collects information through an identity and access management system (IAM). As long as the account is active and the user is frequently accessing it, they will need to update their personal information to keep the data as accurate as possible.
- Data Validation: In order to check the legitimacy of a client or an organization, a data check needs to be performed. This means verifying the validity of the documents your customers provided during onboarding, as well as matching the identity documents to check for any possible discrepancies.
- Customer Identity Proofing: After proving the user’s documents are legitimate, it is necessary to verify their identity. These individuals are trusted with accessing sensitive information or official accounts. The authorized users may also be asked to present additional information, such as usernames, and passwords, as well as proof that they are indeed who they say they are.
This can be done with identity-proofing solutions, such as liveness checks or scanning biometric identity documents.
Why is Identity Proofing Important?
Identity proofing solutions ensure your data is protected, as well as your users’ accounts. Furthermore, it adds an additional layer of security against security threats, for instance, data leaks. Your customers can be sure that only trusted individuals can access the organization’s accounts and manage sensitive information.
In addition, companies can be fined up to $10 billion for not complying with AML and KYC requirements. Therefore, implementing identity proofing in your company’s digital onboarding process will prove to be very cost-efficient. Identity proofing helps your business comply with all mandatory regulations and will prevent your organization from receiving any fines in this matter.
We can see that identity proofing has many features and can be used in multiple contexts. Let’s take a closer look at the types of identity proofing and find out which one fits your organization!
Types of Identity Proofing
As we mentioned before, there are multiple sorts of identity proofing. The most common types are
- Manual identity proofing
- Digital identity proofing
- Data-centric identity proofing
- Biometric identity proofing
They may all resonate with your company in different ways, so it is important to see which one is most suitable for your organization. Here, we created a breakdown of all the types of identity proofing:
Manual Identity Proofing
Manual identity proofing is a knowledge-based authentication form, based on the information the user provides single-handedly. For instance, a user trying to set up an account will provide personal information, such as name, date of birth, and address.
The level of data protection, in this case, is quite weak, as most of the security questions are based on topics such as parents’ names, childhood nicknames, or the name of their first pets.
Usually, the answers to these questions are only known by the user. However, hackers have become better and better at gaining access to this information and breaking into users’ accounts.
Digital Identity Proofing
Digital identity proofing represents an alternative way your users can validate their identity when accessing their accounts. This is done by using their unique ID information in the identity-proofing process.
In most cases, the user is asked to use their ID or driver’s license, but it can also be that additional information is required, such as the last 4 digits of their social security number.
Data-centric
In data-centric identity proofing, the user provides information that validates their existence, in particular, name, address, and social security number. The data is further checked in the respective database to see whether there is a match between the information the user provided and the already existing information.
While it may seem like the checking system is very thorough, this identity-proofing process only proves the existence of a person. Still, it does not identify whether the person providing the information is an imposter or not.
Biometric Identity Proofing


Last but not least, biometric identity proofing is the most secure way to authenticate your identity. It requires unique information, which cannot be duplicated or forged, namely fingerprints, and facial characteristics.
Biometric identity proofing requires the user’s real-time actions to unlock and gain access to their accounts. The procedure involves liveness detection, so the user cannot use a photo or a pre-recorded video of themselves. That is why an additional step is taking a selfie. This verifies whether the person trying to access the account is, in fact, a living person, and not an imposter or a bot.
We have now seen the types of identity proofing and how they work, but there is one more concern that remains, and that is implementing identity proofing solutions in an organization.
To make things easier for organizations, the solution is implementing identity-proofing software. This will help with verifying the identity of your customers in an accurate and safe way, while also protecting the integrity of their data.
But how can identity-proofing software add value to your organization? Let’s take a better look at the benefits of implementing identity-proofing software!
How to Implement Identity Proofing?
To automate ID proofing within your business processes, it is important to first establish how you want to set up your ID proofing process.
The most efficient way of implementing identity proofing is by creating a process that is user-friendly and seamless to integrate into your organization. This process includes steps such as identity document verification, selfie verification, or even a liveness check.
ID document verification using OCR or NFC is done by scanning the biometric chip encrypted in your identity documents. Another option for identity proofing would be biometric verification, which implies taking a selfie and performing a liveness check. This step verifies whether the identity documents belong to the person carrying out the identity-proofing process.
Ideally, users can self-verify and access the authentication process from anywhere, through selfie verification, as long as they have a stable network connection available. This is why companies choose to outsource this process, namely buying an identity proofing software that contains all necessary features and is easy and seamless to integrate with their current systems.
The Benefits of Identity Proofing Software
Identity proofing solutions are a great addition for any company willing to improve its security levels. But besides improving security, it can help with a number of other things that you didn’t consider yet but are deeply important.
Here are some of the benefits that identity-proofing software can offer you:
- Fraud detection: checking customers’ identity against their financial history, can detect fraudulent activities, for example, money laundering.
- Increased customer trust: organizations that add an additional layer of security to their authentication system are more likely to be trusted by their customers.
- Stronger security barrier: adding identity proofing and strengthening the authentication system makes it harder for your organization to be the target of a data leak, keeping it safe from cyber-attacks.
- AML and KYC compliance: comply with AML and KYC requirements by implementing identity proofing and keeping a clear overview of your customers’ activity.
Identity-proofing software adds significant value to your organization and improves all areas regarding data protection, customer trust and satisfaction, and legal compliance.
Therefore, it is important to offer your customers an identity-proofing authentication process that is accurate and easily accessible.
Digital Identity Proofing with Klippa
Many identity-proofing software can bring you great advantages, but they often lack seamless integration with existing applications, affecting the user experience. Using Klippa’s intelligent automated identity verification solution, however, your company can not only benefit from a fast and secure digital onboarding for your customers but from a seamless integration as well.
What else can Klippa do for your organization? These are just some of the benefits of using Klippa’s AI-based identity verification software:
- Identity document scanning: scan any type of identity document with the highest possible accuracy.
- Liveness detection: use a liveness check to avoid spoofing and validate a customer’s identity.
- NFC-based identity verification: read encrypted data from the chip of ID documents and accurately validate the identity of users.
- Biometric identity verification: use biometric verification and accurately identify and validate the identity of users based on unique personal features.
- Age verification: verify users’ age and keep adult-oriented content restricted for users below a certain age threshold.
- Seamless integration: implement the identity verification software through our Identity Verification API or SDK and enjoy the results of a great user experience.
If you want to know more about our intelligent identity verification solutions, our experts would be happy to help you with any questions you might have.
Contact us or request a free demo, and get all the assistance you need, so you too can enjoy the benefits of automation with Klippa!