

In recent years, remote onboarding and authentication have become more popular, providing businesses with greater flexibility and improving customer experiences. However, this shift towards digitalization has also made cyber criminality a serious threat to companies. Global cyber attacks have increased by 38% in 2022 compared to 2021.
One type of cyber attack that companies have to face is called identity spoofing. Identity spoofing occurs when an individual uses various technologies to convince a business that they are someone else. By doing so, they are able to trick the system into believing that they are a genuine user, client, or business. It’s crucial for businesses to prevent it in order to avoid fraudulent activities and ensure that they are dealing with legitimate individuals.
In this blog, we will explain what identity spoofing is, how it occurs in the identity verification process, and provide solutions for protecting yourself and your customers from this type of attack.
What is Identity Spoofing?
In the identity verification process, we can list two types of identity spoofing: Document spoofing and biometric spoofing.
Document Spoofing
Document spoofing involves the replication of an authentic official identity document, like an ID card, with the intent to deceive.
To spoof an ID, fraudsters initially collect personal details about an individual, including their name, address, and email. Subsequently, they meticulously replicate the identity document to closely resemble the genuine original.
This fraudulent document can then be exploited to gain entry to various platforms, accounts, or enterprises, thereby granting unauthorized access.
Biometric Spoofing
Criminals can replicate biometric features, such as facial features, just like they can imitate documents.
For example, it’s possible for individuals to exploit deep fake technology in order to subvert facial recognition systems. This can allow them to gain access to private information by impersonating someone else.
Unfortunately, fraudsters are known to use AI and ML techniques to create fake videos or audio recordings of people, which can be used to deceive or manipulate others. In addition, these individuals may also use a picture of someone else to gain access to a particular platform.
Difference between Identity Spoofing and Identity Theft
You may have heard of identity theft and wondered if it’s the same as identity spoofing. Even though they seem similar, these are two different things:
Identity spoofing involves pretending being someone else to gain access to their personal information or to commit fraudulent activities. The aim is to convince the other party that the person they’re dealing with is trustworthy, so they can gain access to private information from individuals or companies.
On the other hand, identity theft is the act of stealing someone else’s private information, such as their name, address, and date of birth, and using it to commit fraud. The goal is to use this stolen information to make acquisitions or open accounts, for example.
How does Identity Spoofing Occur?
Let’s start by examining the characteristics of an identity spoofing attack. To enhance clarity, we’ll present a concrete real-life illustration.
Spoofing attack context: Let’s say, a banking app offers users the possibility to securely log in using facial recognition technology for convenient and quick access to their accounts.
Spoofing Attack Steps:
- Target Identification: The fraudster selects a target user and gathers public images and videos of the individual from the internet.
- Creation of the fake identity: Using advanced deepfake technology, the fraudster generates a highly realistic and convincing video of the target’s face. The deepfake includes precise facial movements, expressions, and voice replication.
- Attempting to Login: The attacker downloads the app and attempts to log in using the deepfake video as the facial recognition input.
- Authentication Bypass: The facial recognition system of the mobile app is deceived by the deepfake video.
- Outcome: Granting the fraudster unauthorized access to the target’s account.
Spoofing attacks can be attempted during the identity verification process of a company specifically during the onboarding and authentication process.
- Onboarding customers: When a business onboards a new customer, they must verify their identity through a process called KYC (Know Your Customer). This involves asking the customer to provide proof of their identity to ensure that they are who they claim to be. Passports, ID cards, and proof of residence documents are examples of documents that can be asked for during the onboarding. Financial institutions, for example, need to accurately identify customers to prevent financial fraud. Fraudsters may try to pass as trustworthy customers in order to access financial information, so it is important to be vigilant in verifying the identity of new customers.
- Granting access to customers: Once the onboarding process is complete, customers are provided with access to specific services or accounts. Unfortunately, as we’ve seen in the example, fraudsters may attempt to bypass security measures during the authentication process in order to gain access to private information belonging to either the company or its customers.
It may seem frightening, but there’s no need to worry. In the upcoming section, we’ll explain how you can prevent these types of attacks with ease.
How Can You Prevent Identity Spoofing?
Identity spoofing can be a serious issue that often goes undetected until it’s too late. This can result in damages caused by criminal acts.
However, there are efficient ways to prevent this type of fraud. Identity verification software can detect and prevent these attacks effectively.
Prevent Document Spoofing with Automation
By using software, businesses can automatically analyze documents and detect fraud within a short amount of time.
The first step is to provide an image or scan of the identity document to the software. It extracts the information automatically using OCR technology.
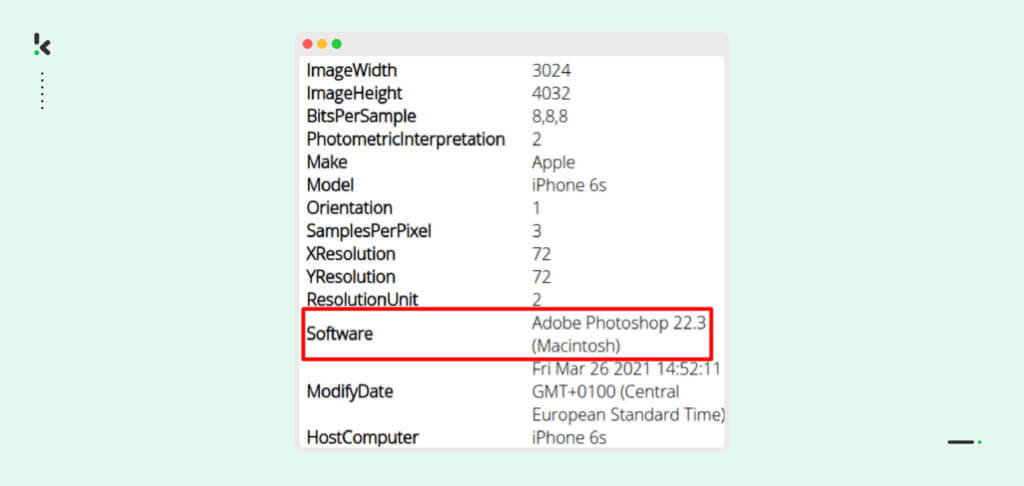
After extraction, the software uses EXIF data analysis to determine the authenticity of documents. EXIF data is also known as “metadata” and provides basic information about the file, including the author, creation date, and file size.
For example, in the screenshot below, the metadata indicates that the file has been opened in Photoshop. This could be a sign that the document was manipulated and the software gives a warning. Such documents can then be double-checked, making it more difficult for fraudsters to use someone else’s identity to access services.

Adding to that, to verify identities, NFC-based verification can be applied. By using NFC technology, you can retrieve customer information from identity documents that contain an RFID chip.
Since the personally identifiable information (PII) stored in RFID chips cannot be tampered with, this enables you to verify the authenticity of the document more effectively. Employing this technology maximizes security, ensures compliance with KYC regulations, and streamlines the onboarding process for customers.
Prevent Biometric Spoofing with Biometric Verification
As we’ve seen in the first section of the blog, biometric features can also be victims of spoof attacks. To prevent it, biometric verification can be performed.
With selfie verification, you can require customers to take and send a selfie using their smartphone. By comparing the selfie with the picture on the identity document, you reduce considerably the risk of identity spoofing.
Additionally, you can add liveness detection to your verification process. During this step, users must perform certain actions to prove their physical presence, such as nodding their head or moving it into a certain direction.
Liveness verification utilizes advanced deep learning technology that can detect fraudulent facial manipulation, including deep fakes. This means that even the most sophisticated deep fake technology used by fraudsters can be identified.
The Benefits of ID Verification Software
- Enhanced security for your business by incorporating automated security measures. Your business and customers will be better protected from fraudulent activities.
- Maintaining the trust of your customers is crucial and can be achieved by ensuring that their data is well-protected. Setting up such measures within your company will help to build trust with your clients.
- Ensuring compliance with regulations by utilizing digital ID verification software. You can easily adhere to KYC and GDPR standards, accurately identify your customers, and safeguard their assets.
- Improve accuracy by using an automated identity verification solution to identify and authenticate your customers. This software can achieve up to 99% accuracy with human-in-the-loop.
Prevent Identity Spoofing with Klippa
As a business, preventing identity spoofing can be a difficult task. At Klippa, we recognize this challenge and have developed a smart solution to help you prevent these attacks. We offer a solution for stress-free onboarding and authentication processes for your valuable customers.
Klippa can verify the authenticity of documents within seconds. Our software is equipped with:
- Liveness detection and selfie verification, to protect against identity spoofing.
- EXIF data analysis to quickly detect any fraudulent documents.
- NFC checks to get 100% accuracy.
- SDK and API to implement easily our software into your app or platform.
Curious to know more about our solution? Please, feel free to contact us or book a live demonstration below!