

Protecting personally identifiable information (PII) has become a top priority for businesses collecting and storing vast amounts of customer data. Companies must prioritize data security to stay compliant and show customers their trust is valued.
In 2023, the United States experienced 3,205 data compromises, affecting over 353 million individuals. Nearly half of these breaches exposed PII, such as names, social security numbers, and financial details. These staggering numbers highlight the critical need for organizations to implement robust data protection measures.
The solution lies in PII masking, a way of covering up personal details, like names or social security numbers, to keep data secure and useful. This blog will unpack the concept, explore its mechanisms, and explain why it’s essential for modern businesses.
What is PII Masking?
PII (Personally Identifiable Information) masking is a data protection technique that hides sensitive personally identifiable information to prevent unauthorized access. It keeps the data functional for approved use cases by replacing or covering details like names, social security numbers, credit card information, and addresses. This ensures that data remains secure and usable for testing, analysis, or internal operations, while also contributing to anonymization efforts.
Unlike encryption, which locks data and requires a key to read it, masking changes sensitive information into a realistic-looking version that can’t be traced back to the original person. For example, a real name like John Doe might be masked to J*** D**, or a social security number like 123-45-6789 could become XXX-XX-6789.
PII masking is widely used in industries such as finance, healthcare, and retail, where protecting customer data is both a legal obligation and a vital step toward building trust. By implementing PII masking, organizations can comply with data privacy regulations like GDPR and CCPA while continuing to extract value from their datasets.
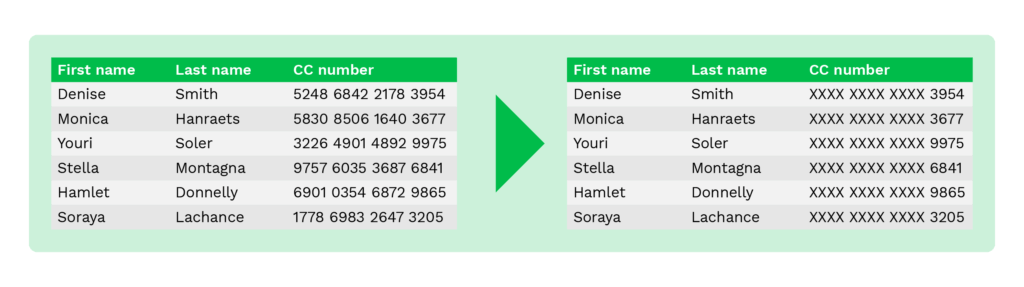

How Does PII Masking Work?
In the previous section, we discussed PII masking and its importance. Now, let’s walk through the process step by step to understand how PII masking works.
Step 1: Identifying and Classifying Sensitive Data
The first step in PII masking is identifying and categorizing sensitive information, such as names, social security numbers, credit card details, and addresses, within your documents, databases, or systems. This ensures that all personal data requiring protection is flagged for masking.
Step 2: Using OCR to Extract and Detect PII from Non-Editable Formats
For documents in non-editable formats like PDFs or scanned images, Optical Character Recognition (OCR) technology is used to extract text and identify PII. OCR ensures that even unstructured or document-heavy workflows do not leave sensitive information overlooked.
Step 3: Validating and Mapping PII Data
Before masking, the identified data is validated and mapped to ensure consistency and accuracy. This step ensures that all instances of sensitive information are properly accounted for, including duplicates or cross-referenced fields in interconnected systems.
Step 4: Selecting the Appropriate Masking Technique
Businesses then choose a data masking technique tailored to their specific use case. For instance, static masking or dynamic masking.
Step 5: Masking the Sensitive Data
Once the technique is selected, the actual masking is applied to the identified PII. This step transforms sensitive data into secure, obfuscated values while retaining usability for tasks such as testing, analytics, or operational workflows.
Types of PII masking
There are different PII masking techniques available. Below, are the most common types of PII masking and how they work:
Static masking
Static masking permanently replaces sensitive data with masked values in a non-production environment, such as test or development systems. It ensures that data remains protected but still looks realistic for testing or training purposes.
Dynamic Masking
Dynamic masking hides sensitive data in real-time while leaving the original data unchanged. Unauthorized users see masked values based on their access permissions, while authorized users can view the real data.
Tokenization
Tokenization replaces sensitive data with random tokens that have no usable value on their own. The original data is stored securely elsewhere and can only be retrieved using a secure mapping process.
Format-Preserving Masking
This method keeps the structure and format of the original data intact while masking its content. It’s useful for systems that require specific formats, such as dates or credit card numbers.
Encryption-Based Masking
Encryption transforms data into unreadable ciphertext that can only be decrypted with a secure key. It is ideal for protecting data during storage or transfer.
Data Redaction
Data redaction removes or blacks out sensitive information entirely, making it unreadable and irretrievable. This method is commonly used for documents like PDFs.
Substitution Masking
Substitution masking replaces sensitive data with fictional but realistic-looking values. It helps preserve data usability while protecting privacy.
Nulling Out
Nulling out replaces sensitive fields with blank or null values, effectively removing the data. It’s useful for fields that don’t need to be displayed to users.
PII data masking techniques explained
Now that you know the different types of techniques, below is a table that provides a clear overview of the most common masking techniques and their key features, helping you understand how these techniques work.
Why Should You Use PII Masking?
In the previous section, we explored how the different PII masking techniques work to protect sensitive information. Now, let’s examine its benefits and why PII masking is essential for your organization.
Ensure Compliance with Data Privacy Regulations
Laws like GDPR, CCPA, and HIPAA require organizations to safeguard PII. Failure to comply can result in strict penalties, reputational damage, and loss of customer trust.
- Example: GDPR requires businesses to implement measures to protect EU citizens data. PII masking helps ensure compliance by securing personal information against unauthorized access.
Minimize Data Breach Risks
Even with robust security measures, data breaches can happen. PII masking significantly reduces the risk of exposing sensitive data if unauthorized access occurs. Masked data has little to no value for attackers, helping protect both customers and your organization.
- Example: If a dataset is compromised, the masked information cannot be traced back to individuals, reducing potential harm.
Protect Customer Trust and Reputation
Data breaches incur financial losses and damage customer confidence. Businesses that actively prioritize data privacy, such as through PII masking, demonstrate their commitment to protecting customers’ sensitive information.
- Example: By safeguarding PII, you build stronger relationships with customers, enhancing brand loyalty and reputation.
How Klippa can help with PII masking
Klippa provides a powerful and easy-to-use IDP solution for PII masking, enabling businesses to protect sensitive data with ease. It ensures compliance with privacy regulations like GDPR and CCPA while maintaining data security. With Klippa, you can anonymize in bulk and implement different types of masking techniques to protect data during transfers, testing, or analysis.
Our AI-powered platform automatically identifies and classifies sensitive data, ensuring full accuracy and consistency across systems. Whether it’s organizing data at the source or masking information in real-time, Klippa offers seamless integration with existing workflows and scalable solutions to grow your business.
By using Klippa’s PII masking solutions, you can protect customer trust, reduce compliance risks, and focus on what matters most: serving your clients and growing your business.
Ready to simplify PII masking and boost compliance? Schedule a free demo or contact us today!
FAQ
PII masking is a data protection technique that hides sensitive personally identifiable information (PII) to prevent unauthorized access. It ensures that businesses can secure data while still making it usable for tasks like testing, analysis, or operational workflows.
What types of data can be masked with PII masking?
PII masking can be applied to various types of sensitive information, such as: Names, Social Security Numbers (SSNs), Addresses, Credit card details, Phone numbers, Bank account numbers, Email addresses and much more.
How does OCR technology assist in PII masking?
OCR (Optical Character Recognition) technology helps extract and identify PII from non-editable formats like PDFs or scanned documents. It ensures that even unstructured data in document-heavy workflows is properly flagged for masking, leaving no sensitive information unprotected.
How can Klippa help with PII masking?
Klippa provides an advanced IDP solution that automates PII masking using AI-powered tools. It can identify and classify sensitive data, implement various masking techniques, and ensure compliance with regulations like GDPR and CCPA. Klippa offers scalable, easy-to-integrate solutions for secure and efficient data management.